This article discusses the identity theft prevention program which mortgage loan originators (MLOs) and mortgage loan brokers (MLBs) are to implement under the federal Red Flags Rule.
Applications and credit reports for borrowers seeking mortgage funds are consistently received by:
- mortgage loan originators (MLOs) of consumer mortgages; and
- mortgage loan brokers (MLBs) of business mortgages.
This personal information is collected from applicants as a crucial part of arranging any mortgage. The information ensures that mortgage funds are disbursed to the correct person and actually secured by the subject property, all part of a mortgage lender’s risk management. Prudent processing of a mortgage origination requires a complete profile on the borrower and their ownership of the real estate which will be security for the mortgage debt.
However, identity theft poses a threat to the integrity of all mortgage originations.
As the first point of contact with a borrower, MLOs and MLBs are in perfect position to reduce these risks.
Federal regulations step in to reduce the risk
The Red Flags Rule was developed by the Federal Trade Commission (FTC) to mitigate identity theft risks borrowers of mortgages are exposed to when a mortgage is made or arranged by MLOs and MLBs.
Proprietary and corporate brokers who are MLO and MLB business operations need to implement written procedures and checklists for screening mortgage applications, referred to as an Identity Theft Prevention Program (ITPP). The procedures are required to help MLOs and MLBs adequately detect suspicious activity and indications of potential fraud, called “red flags,” in mortgage applications and other documents provided by an applicant. [15 United States Code §1681 et seq]
Implementation of written procedures for detecting suspicious activity requires the MLO or MLB business operation to:
- screen mortgage applications and related documents for typical signs of fraud and identity theft; and
- protect the personal information of applicants and, if servicing mortgages, current borrowers from identity theft.
Applying the rule to MLO and MLB businesses
MLOs and MLBs are subject to the Red Flags Rule when, in their course of making or arranging mortgages, they also:
- obtain or review credit reports relating to any type of mortgage origination;
- provide information to credit reporting agencies; or
- advance mortgage funds themselves — whether from their own funds or under a warehouse line of credit — or on behalf of a lender. [15 USC §1681m(e)(4)]
The rule initially targets MLOs who make, arrange or service mortgages which fund primarily personal, family or household purposes, called consumer mortgages. However, MLBs making or arranging business mortgages are also required to create procedures to prevent fraud when the mortgages they make present a reasonably foreseeable risk of identity theft, such as those that may result from data accessible by telephone or the internet. [16 CFR §681.1(b)(3)]
Nonetheless, as good business practice and risk management, all MLBs are advised to implement procedures for reviewing mortgage applications and detecting suspicious activity, regardless of the level of risk they determine exists.
In addition to following their own written procedures, MLOs and MLBs acting as service providers for a lender also need to follow any procedures imposed by the lender as part of its security requirements for detecting mortgage fraud. [16 CFR §681, Appendix A(VI)(c)]
Further, all MLBs and MLOs are uniformly required to have policies for verifying a borrower’s identity upon receiving an address discrepancy notice from a credit reporting agency. [16 CFR §641.1]
Written procedure basics
Simply put: compliance with the Red Flags Rule requires the development of specific procedures by MLOs/MLBs for their critical review of mortgage applications and documents to detect activity that may indicate fraud or identity theft. Thus, individual MLO and MLB agents need to be familiar with their company’s written program and understand how to recognize risk factors.
Typically, this requires:
- an understanding of what constitutes suspicious activity;
- how to spot discrepancies in information provided by an applicant; and
- how to properly screen all mortgage applications and related documents.
To help MLO and MLB agents to implement these requirements for their employing broker, the written documentation of a company’s checklists and procedures need to:
- identify activities, errors, discrepancies and documents that indicate fraud or identity theft;
- outline the process for detecting suspicious activity when reviewing applications and documents;
- clarify how to respond to indications of fraud when discovered; and
- explain how to update the procedures periodically to reflect changes in risks to borrowers or the company (e.g. by adding any new type of activities deemed indicative of fraud or identity theft). [16 CFR §681.1(d)(2)]
Identifying and detecting suspicious activity
To determine what type of activity is suspicious and may indicate fraud, MLOs and MLBs are required to gauge the risk factors in the mortgages they originate, including:
- the types of mortgages offered;
- methods used to make and access mortgages; and
- their previous experience with identity theft and fraud. [16 CFR §681 Appendix A(II)(a)]
They may draw from past incidents of identity theft, any changes in identify theft risks they have identified and supervisory guidance given about what type of activity is suspicious or new methods used by fraudulent applicants.
The use of a checklist containing activity identified as suspicious is required to determine whether an applicant’s information indicates fraud. However, the content of the list will vary by company and is to be set out in writing by each MLO/MLB company.
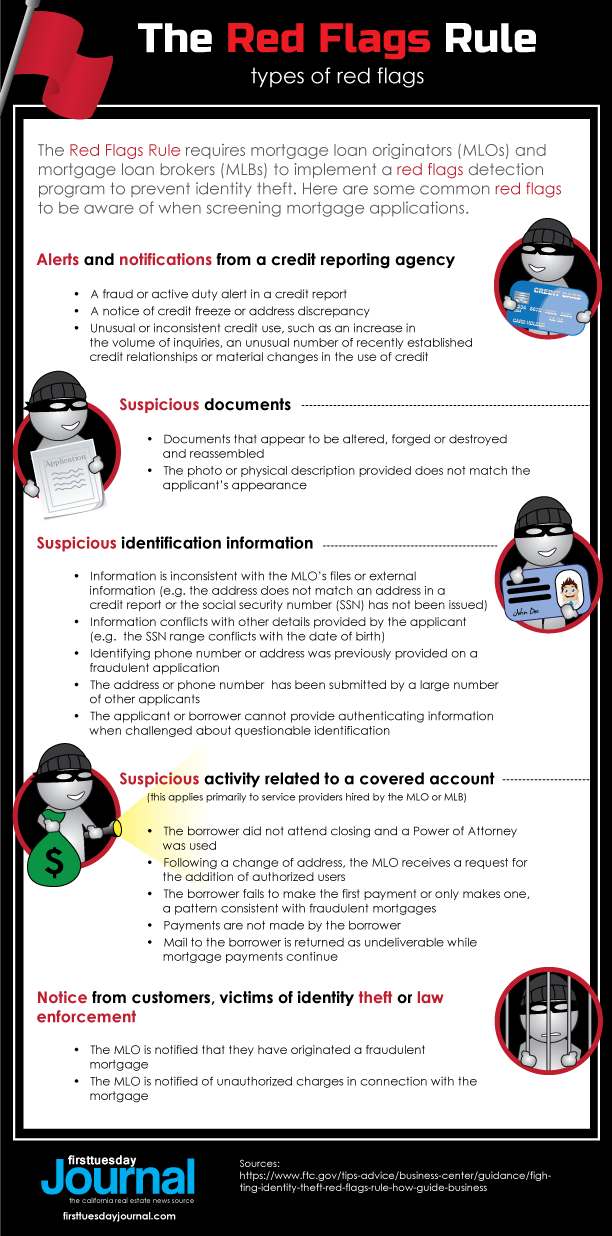
Examples of activity that may be added to the checklist as indications of fraud include:
- alerts or warnings from credit reporting agencies or service providers, such as fraud detection services;
- suspicious documents that appear to be altered or forged;
- suspicious personal identifying information, such as a peculiar address change;
- unusual activity related to a mortgage; and
- notice from borrowers, victims of identity theft, law enforcement or other persons regarding potential identity theft related to a mortgage. [16 CFR §681, Appendix A(II)(c)]
MLOs and MLBs are to further screen mortgage applications by:
- obtaining and verifying personal information about a mortgage applicant; and
- monitoring transactions and verifying the validity of any change of address requests for existing mortgages they service. [16 CFR §681, Appendix A(III)]
Responding to suspicious activity observed
Once suspicious information is detected in an application or other related document, MLOs and MLBs need to have a process for responding to indicators of identity theft by:
- monitoring for errors and suspicious activity when servicing the mortgage;
- contacting the applicant or borrower;
- changing passwords, security codes or other security devices that allow access to the mortgage or application;
- reopening a mortgage with a new account number;
- closing an existing mortgage;
- withholding collections on a mortgage and not selling it to a debt collector;
- notifying law enforcement; or
- determining no response is needed under the circumstances at hand. [16 CFR §681, Appendix A(IV)]
To determine which response is the most appropriate, MLOs and MLBs need to assess each mortgage on a case-by-case basis. Responses will depend on the procedures presented in the company’s Red Flag fraud detection manual.
For example, if an MLO or MLB observes a fraud alert situation on a credit report, they need to take extra care to compare identification documents and photos provided by the applicant with other documents on file. If multiple addresses on the credit report are different from the address of the applicant’s property, the MLO or MLB may use the county’s assessor, appraiser or tax collector web site to verify the ownership of the property located at the common address given to them.
In addition to the requirements of the Red Flags Rule, some common actions to take when evidence of identity theft is discovered include:
- filing a Suspicious Activity Report (SAR) (e.g. in the case of suspected mortgage fraud or money laundering) [31 USC 5318(g)];
- confirming the identity of the person applying for the mortgage when a fraud alert is included on a credit report [15 USC §1681c-1(h)];
- abiding by requirements for furnishing accurate information to credit reporting agencies [15 USC §1681s-2]; and
- complying with the prohibitions on the sale, transfer and placement for collection of certain debts resulting from identity theft. [15 USC §1681m]
Oversight and procedure updates
As part of the administration requirements, the MLO or MLB company needs to:
- obtain written approval of the procedures from either a board of directors or designated officer/employee in senior management;
- include the board of directors or designated officer/employee in oversight, development and implementation of procedures; and
- provide oversight of any service providers by requiring them to also follow risk management procedures. [16 CFR §681.1(e)]
Proper administration of the written program requires the board of directors, committee of the board or a designated officer/employee in senior management to establish annual reports for their review of suspicious activity and staff responses. [16 CFR §681, Appendix A(VI)]
The annual reports are evaluated for the effectiveness of the company’s procedures in addressing identity theft risks. Material changes may need to be recommended, such as how MLOs/MLBs review applications or what types of activities and documents are deemed suspicious by their written checklists. [16 CFR §681, Appendix A(VI)(b)]
To assess whether changes are needed, an MLO or MLB is encouraged to consider:
- their experiences with identity theft;
- changes in methods of identity theft and its detection, prevention and mitigation;
- changes in the types of mortgages the MLO or MLB offers or maintains; and
- changes in the business arrangements of the credit, including mergers, acquisitions, joint ventures and service provider arrangements (e.g. transitioning the credit to a warehouse line). [16 CFR §681, Appendix A(V)]
Further, management of the written program requires oversight of service providers used to perform activity in connection with a mortgage to ensure they are also compliant with the Red Flags Rule. This includes credit-checking services, contract processors, notaries and document storage companies. [16 CFR §681, Appendix A(VI)(c)]
For example, an MLO may require a service provider, by contract, to implement policies for detecting signs of fraud encountered during the service provider’s activities and reporting them to the MLO or mitigating identity theft themselves.
Penalties for noncompliance
When an MLO or MLB company fails to comply with the Red Flags Rule, the FTC has the authority to:
- investigate the person or business in violation;
- enforce compliance through issuing procedural rules for detecting suspicious activity; and
- require the filing of reports, the production of documents and the appearance of witnesses. [15 USC §1681s(a)(a)]
Further, the FTC may commence a civil action against those in violation to recover civil penalties of up to $3,500 per violation. [15 USC §1681s(a)(2)(A); 17 CFR §1.98]
In determining the amount of a civil penalty, the court considers the degree of the violation, any history of similar prior conduct, ability to pay and effects on the ability to continue to do business. [15 USC §1681s(a)(2)(B)]
Check out our graphic below for example “red flags” to watch out for: